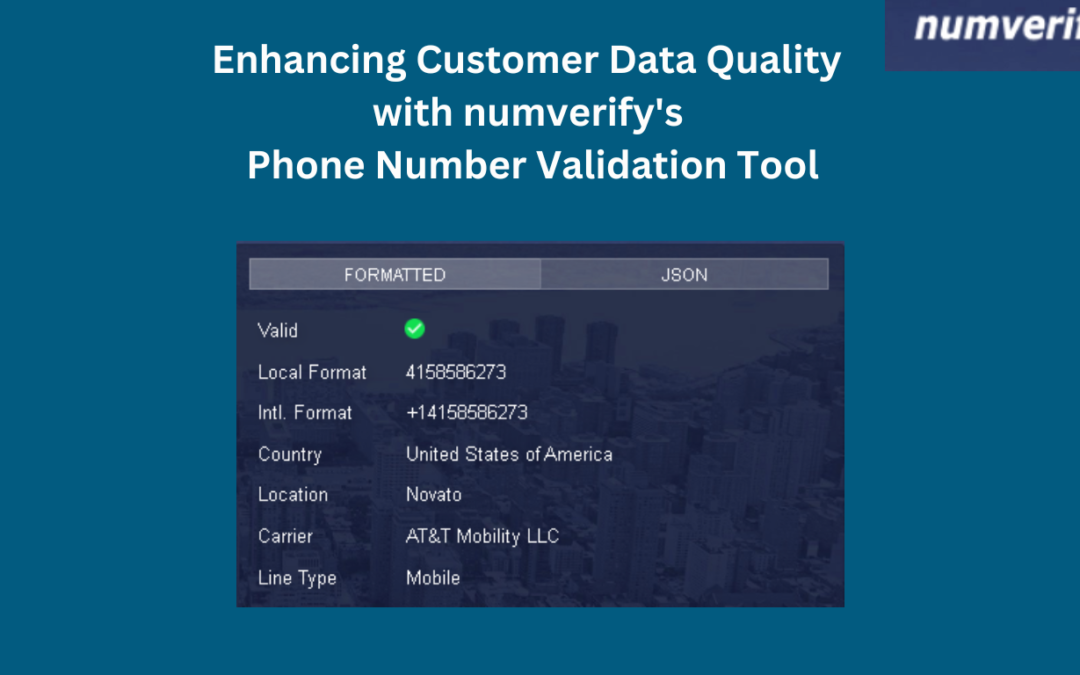
Customer data is like a gold mine for businesses. For example, companies collect customers' contact information to personalize customer experiences, improve customer support services, send promotional offers, and enhance their marketing campaigns. This, in turn, helps...